Cybersecurity: Keep Your Firm’s and Clients Data Safe
As firms are entrusted with lots of sensitive (and legal) information, cybersecurity is a must. Learn about the different types of cyberattacks and download a FREE cybersecurity protocol.
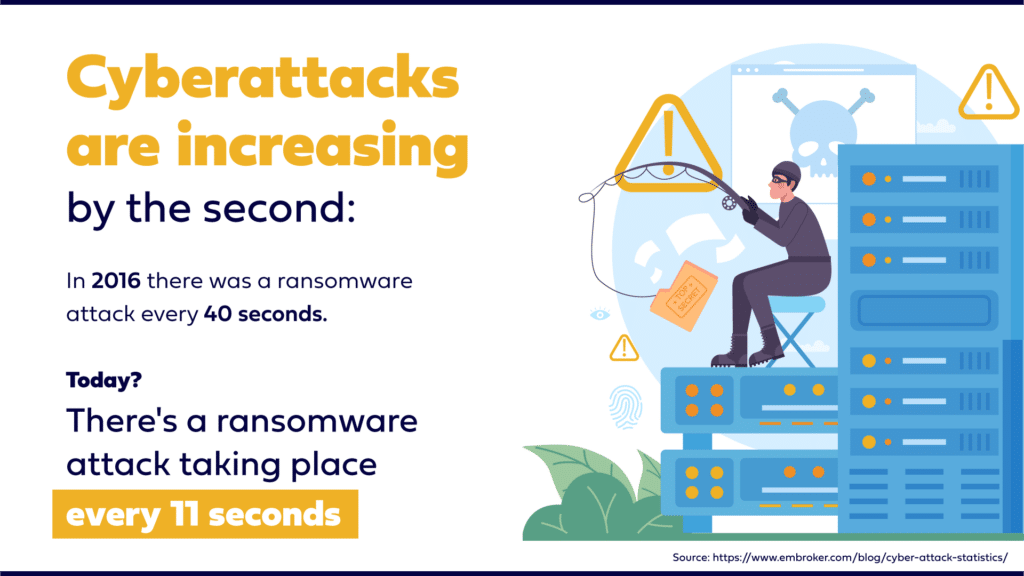
The truth is cyberattacks can happen to any business and can be costly for those who aren’t prepared. Research finds that cyber crimes are increasing and costing trillions of dollars. Specifically, worldwide cybercrimes are set to cost over $10.5 trillion by 2025, up more than 3X the $3 trillion reported in 2015.
Source: https://www.embroker.com/blog/cyber-attack-statistics/
Our intent is not to alarm you by sharing those figures; but rather to inform you about the real danger posed by cyberattacks so you can arm your firm against potential threats. In today’s climate, most of our work is based on and even stored in digital platforms. Moreover, clients are demanding higher quality service propelled by new technological services. The simple truth is that the way we do business today puts us at risk of being the victim of a cybercrime.
If you’re thinking, ‘why would someone want to hack my firm and want all of my ‘boring’ clientele’s information?’ The answer is: hackers know how to get to what they’re looking for. They can get past ‘the boring information and get to the gold: your customer’s name, address, social security numbers, dates of birth, and credit card information.
Protecting your firm from such attacks is serious business. Stay with us and learn about cybersecurity, from the different types of cyberattacks to the best ways to arm your firm.
Know Your Enemy: Types of Cyber Attacks & Counter-Attacking Methods
Sun Tzu, the credited author of ‘The Art of War, ‘ said, “If you know the enemy and know yourself, you need not fear the result of a hundred battles.” Awareness is fundamental when trying to predict your attackers’ actions. The same goes for cyberattacks; you need to know your enemies to defeat them.
These are the main types of cyberattacks:
1. Malware attacks
What it is:
Malware attacks are designed to cause damage to a system. Some examples of malware attacks include ransomware attacks and viruses. Tom Kirkham, founder and CEO of Kirkham.it and Iron Tech Company, recently sat down as a guest in our LAWsome podcast and spoke about “Cybersecurity for Lawyers: Repel Cyberattacks and Protect Your Firm’s Business.”
Here’s a small snippet with his take on ransomware attacks:
What you can do about it:
- Keep your operating system, e.g. Windows or Apple, up to date.
- Keep all firewalls up to date.
- Train your staff on how to recognize an attack.
2. Friday afternoon fraud
What it is:
A type of phishing attack that is common in the legal profession. Usually, criminals hack into email accounts between a client and you and may pretend to be you and ask for payment details, etc.
It’s called Friday afternoon fraud because many transactions occur during this time, but it can happen any day of the week.
What you can do about it:
- Tell your clients to please steer away from any public wifi when sending/opening sensitive emails.
- Interchange banking details between your firm and client from the first meeting you partake in person.
- Confirm payment before and after the client sends money via a phone call, in person, through a secure payment portal, etc.
3. Phishing
What it is:
Usually, the scammers pose as trustworthy people, e.g., police or bankers. They’ll usually attack through emails but might also scam people through phone calls, texts, and socials.
What you can do about it:
- Only open the emails and attached files from trusted sources. If it looks fishy, it might be some form of phishing.
- Take a look at the links, and when in doubt, don’t be afraid to contact the sender to verify.
4. Vishing
What it is:
Similar to phishing, except it’s solely for phone-based scams. Likewise, the criminal will pose as someone trustworthy, e.g., police or bankers.
What you can do about it:
- Never give out your banking details; banks will never ask for this type of information via email or phone calls.
- Provide your clients with all banking details in the first meeting, in person.
- Train your staff to recognize scam calls and provide details on what to do next, e.g., ask to be removed from the caller list. Legally, the caller is required to do that. However, they’ll likely keep calling if it’s a scam.
5. Data breach
What it is:
Releasing private unauthorized information into uncontrolled environments like the Internet.
Unlike the other types of cyberattacks, a data breach can also be accidentally caused by someone on your staff! It can happen when a staff member sends sensitive data to the wrong person/email or when an encrypted device or paperwork is lost/stolen. This is why everyone at your firm must know how to handle sensitive information and what to do in the worst-case scenario.
What you can do about it:
- This type of cyberattack is considered high risk and you’ll need to raise awareness all around. In the USA, you can report data breaches as well as any other type of cyberattack using the following 3 links:
6. Supply chain attacks
What it is:
A hacker is looking to control sensitive data or funds linked to a system with the least protection (this is usually the case for small businesses).
What you can do about it:
- Vet all your firm’s software and devices before use (preferably by IT).
- Keep your operating system, e.g. Windows or Apple, up to date.
- Keep all firewalls up to date.
- Make sure old devices no longer in use are completely emptied and disconnected from Bluetooth and Wifi networks.
Cybersecurity Protocol to Train Your Firm’s Staff
We’ve provided some valuable tips based on each type of cybercrime. If you’d like to better arm your firm, download our FREE cybersecurity protocol with the top 6 best practices your firm can implement starting today!
Download My New Cybersecurity Protocol
Prepare for the Unexpected
As you update your firm’s services with new technology, you must have the appropriate safety layers in place. This is especially the case for firms working with third-party vendors, as they have access to a firm’s backdoor website, socials, passwords, sensitive data, and more.
At Consultwebs, we’re not leaving any backdoors open for cybercrimes. Whether you’re looking for a reliable agency, want to ask more questions, or want to secure all your channels feel free to reach out to us.